You have spent months perfecting your business app that could revolutionize your industry. Launch day arrives, user adoption exceeds expectations, and everything seems perfect. Then you wake up to see your company’s name trending, not for innovation, but for a catastrophic security breach that’s making national headlines.
That nightmare became reality for too many organizations. In June of this year, United Natural Foods Inc. (UNFI) watched helplessly as a cyberattack brought their grocery deliveries to a halt. They were exposed to critical vulnerabilities across North America’s food supply chain.
Last year, McLaren Health Care in Michigan faced the devastating task of notifying over 743,000 patients that their personal and medical information had been exposed in a ransomware attack. Meanwhile, these aren’t outliers: Sepah bank’s compromise of 42 million customer records.
Here’s what these breaches have in common: Each organization likely had security measures in place: firewalls, scanners, compliance checkboxes. Yet they still made headlines for all the wrong reasons.
The truth? Traditional and semi-automated DevSecOps approaches that worked five years ago are now creating the very vulnerabilities they are meant to prevent.
Your security tools might be generating thousands of alerts while missing the threats that matter. Your development teams might be choosing between shipping fast or shipping secure, not realizing they can achieve both.
As a tech-savvy business owner, these headlines are your wake-up call and you should learn the latest trends in the DevSecOps to protect your business data. According to a survey, the global DevSecOps market size is projected to grow from USD 3.7 billion in 2023 to USD 18.2 billion by 2032, with a CAGR of 19.3% during the forecast period.And the latest technologies always changing the trends.
That is why, in this blog, we are going to reveal fifteen transformative DevSecOps trends that you should know to stay off the breach list. Ready to turn security from your biggest liability into your competitive advantage? Let’s dive in
Key Takeaways
- Security must shift from being a final checkpoint to an integrated part of the entire software development lifecycle process.
- Proactive vulnerability management prevents costly code rewrites and emergency fixes with early detection during the development.
- Compliance and regulatory requirements need consistent security configurations.
- Risk assessment must be dynamic and continuous rather than periodic manual exercise.
- Integration with existing development tools and workflows is essential for security adoption.
1. AI-Driven Security Automation
Traditional manual security reviews have different issues in modern development cycles. Security teams struggle to keep pace with rapid deployment schedules. As a result, your security team discovers vulnerabilities only after they have reached production. This ‘reactive approach’ leaves organizations exposed to threats!
However, AI-driven security automation transforms this paradigm with ‘intelligent threat detection’ directly. Machine learning algorithms (predictive analysis) continuously analyze code commits, runtime behaviors to identify potential security risks in real-time. Some of the key benefits are:
- 24/7 automated threat detection without human intervention
- Faster time-to-market with security built into IDEs and CI/CD pipelines
- Reduced operational costs through intelligent alert prioritization
- Proactive vulnerability management before production deployment
The business impact? The development velocity increases and security strengthens because attackers are also using AI, so you need better monitoring and updating of your security solutions.
2. Autonomous Remediation
Another challenge of the traditional vulnerability response cycle is that it creates dangerous exposure windows that can cost businesses millions! When security issues are discovered, organizations face a cascading series of delays due to manual process. It usually takes days or weeks.
Autonomous remediation systems eliminate these gaps: these intelligent platforms identify vulnerabilities and automatically reconfigure security controls without human intervention. Autonomous remediation solutions are often integrated into Application Security Posture Management (ASPM) platforms for centralized visibility and orchestration across code, deployment, and runtime stages. Here are the key advantages of using autonomous remediation:
- Mean time to remediation reduced from hours to seconds
- Eliminate human errors in critical security responses
- 24/7 protection without additional staffing costs
- Maintained business continuity during security incidents
The business value extends beyond risk reduction. Companies can maintain continuous operations without the operational overhead. Development cycles remain uninterrupted, and security incidents no longer trigger costly all-hands meetings.
3. Shift-Left Security
Vulnerability assessment is not a final checkpoint anymore! When security issues surface late in development, teams face expensive code rewrites. This approach transforms security from a protective measure into a business liability. It has a consolidated, AI-enhanced toolchain that allows cross-team visibility, self-healing systems, and cloud-to-code traceability.
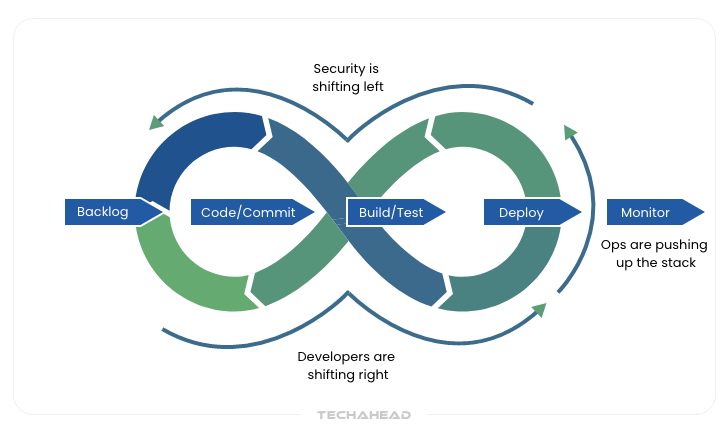
Shift-left security integrates security testing directly into the development workflow from the initial coding phase. It means the use of AI for automated risk prioritization and encompasses containers, and serverless, not just app code. Developers receive immediate feedback on security issues through IDE plugins, automated code analysis, continuous security scanning in CI/CD pipelines.
For example, Netflix uses shift-left security that allows them to deploy thousands of code changes daily maintaining the security standards of global streaming infrastructure.
4. Zero Trust Architectures
Traditional perimeter-based security models operate on the flawed assumption that threats exist only outside the network boundary. Once users or devices authenticate past the firewall, they gain broad access to internal systems. This “trust but don’t verify” approach creates massive security blind spots.
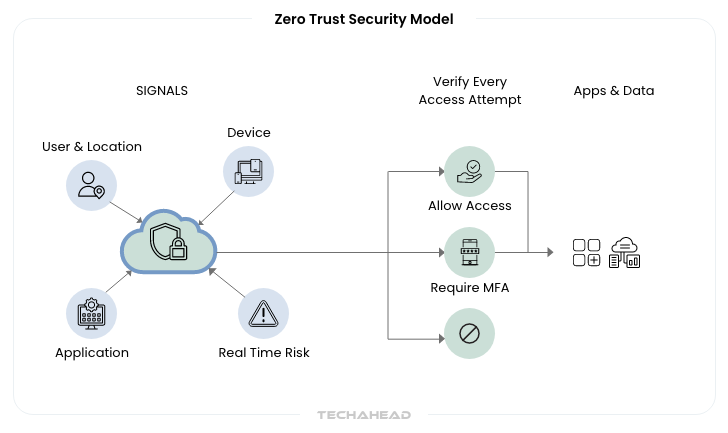
However, with Zero Trust architecture, it eliminates implicit trust by requiring continuous verification of every user, device, and application attempting to access resources. Indeed, every access request undergoes real-time authentication, regardless of previous access history.
For example, Google pioneered zero trust with their BeyondCorp initiative, which eliminates their corporate VPN. Their employees access internal applications from any device or location through identity-aware proxies that continuously validate access requests.
5. Cloud-Native Security
The migration to cloud infrastructure exposed fundamental limitations in traditional security approaches. Legacy security tools struggle with the dynamic nature of cloud resources. Cloud-native security solutions are architected specifically for modern cloud paradigms.
These platforms automatically discover and secure new resources as they are deployed, integrating directly with cloud APIs for real-time visibility. Besides that, you can get advantages like container orchestration, serverless execution models, cloud-specific attack vectors that traditional tools cannot address.
This latest trend Integrates Cloud-Native Application Protection Platforms (CNAPPs) that unify Cloud Security Posture Management (CSPM), Cloud Workload Protection (CWP), and Infrastructure as Code (IaC) security into a single platform and helps you fully leverage cloud agility without sacrificing security of your business information.
Capital One rebuilt their security architecture using cloud-native principles after their AWS migration. Their security platform automatically protects new cloud resources, and provides real-time threat detection across their entire multi-cloud infrastructure.
6. DevSecOps as a Service (DaaS)
Building in-house DevSecOps demands investment. It means, skilled professionals command premium salaries. Moreover, small and mid size companies often struggle to maintain current threat intelligence.
However, DevSecOps as a Service eliminates these barriers with enterprise-grade security. DaaS platforms offer security integration including automated code scanning and threat detection; all through cloud-based infrastructure.
These services provide immediate access to security expertise with the latest tools. Salesforce relies on Snyk’s managed security services to automatically detect vulnerabilities in code. The benefit? For your business, you can optimize the operational costs and get access to specialized security knowledge.
7. GitOps & Security as Code
Generally, security management relies on manual configuration changes, and ad-hoc policy updates. It means inconsistencies, lack of change visibility, coordination difficulty. GitOps transforms security management by treating security policies, configurations, and infrastructure as code stored in version-controlled repositories.
Security controls become reviewable, and automatically deployable through standard development workflows. Changes undergo peer review, automated testing, and approval processes before deployment. You can expect the following capabilities:
- Complete audit trails for all security configuration changes
- Instant rollback capabilities when issues are detected
- Automated policy enforcement across all environments
- Collaborative security reviews through standard Git workflows
The business impact is particularly significant for regulated industries where compliance documentation is complex. You can consider GitOps & Security as Code for security consistency across the entire infrastructure lifecycle.
8. Infrastructure as Code (IaC) Security
Now regular infrastructure management involves manual server provisioning, network configuration, security policy implementation. When you rely on manual processes, security configurations become inconsistent. However, Infrastructure as Code Security integrates security policies directly into automated infrastructure provisioning workflows.
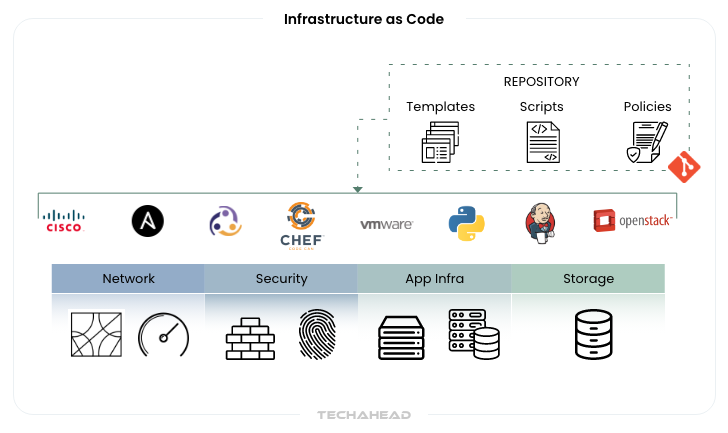
Security rules, compliance requirements, and configuration standards are codified across all deployed resources. Automated scanning continuously monitors for configuration drift that provide real-time alerts when systems deviate from approved security baselines. Here you can expect the following security advantages:
- Automated enforcement of security policies during infrastructure deployment
- Continuous monitoring and detection of configuration drift
- Version-controlled security configurations with complete change history
- Consistent security baselines across development, staging, production.
Moreover, you can scale infrastructure rapidly and respond to security incidents with automated remediation. This approach is suitable for finance, healthcare, ecommerce and regulated industries.
9. Cross-Team Security Collaboration
Development teams often view security as a roadblock, while security teams lack visibility into development priorities. Traditional security models create organizational silos and friction that slows threat response.
Cross-team security collaboration breaks down these silos with unified communication channels, and collaborative incident response. Security becomes a shared responsibility across all teams and you can expect real-time visibility into incident status.
In short, you get faster incident response (reduced downtime) and improved collaboration for better feature delivery.
10. Continuous Threat Modeling
Regular threat modelling approaches treat security risk analysis as a manual exercise. In most cases, these approaches are reactive. However, continuous threat modeling transforms this reactive approach directly into CI/CD pipelines.
Every code commit, infrastructure change, and architectural modification triggers automated threat assessment using established frameworks like STRIDE or PASTA. This integration identifies potential attack vectors before they reach production environments.
Core automation capabilities include:
- Automated threat detection integrated into every code commit
- Dynamic risk assessment based on architectural changes
- Version-controlled threat models that evolve with application development
- Real-time security feedback during the development process
In the financial sector it is playing a vital role. For example, Charles Schwab implemented ThreatModeler’s automated threat modeling platform to protect their applications (and infrastructure) and reduce the burden on security. It helps them scale their security assessments across their entire financial services portfolio without proportionally increasing security team headcount.
11. API Security
Modern digital ecosystems depend heavily on APIs to connect applications, services, and data across internal systems and external partners. However, APIs often become the weakest link in security architectures. It is true that manual API security assessments cannot keep pace with rapid development cycles.
However, API security automation addresses these challenges throughout their lifecycle. Automated scanning tools integrate directly into CI/CD pipelines for analyzing API specifications before APIs reach production environments.
Automated API security allows rapid innovation while protecting sensitive data. Companies safely expand their digital ecosystems, integrate with partners, and launch new services without the risk of exposing their business assets.
12. Enhanced Open-Source Security
Modern applications contain many open-source components; each dependency can have potential vulnerabilities, and manual tracking becomes impossible! The SolarWinds attack showed how compromised supply chains devastate entire organizations.
Moreover, Automated Software Composition Analysis (SCA) tools continuously scan codebases, identifying vulnerable dependencies the moment they are introduced.
These platforms provide real-time vulnerability alerts and automated remediation recommendations integrated directly into development workflows.
With enhanced open source security, you can expect the following capabilities:
- Automated dependency vulnerability scanning in CI/CD pipelines
- Real-time alerts for newly discovered vulnerabilities in existing components
- License compliance monitoring to prevent legal risks
- Supply chain integrity verification for all third-party components
With enhanced features, you can confidently leverage open-source innovation to maintain security compliance without compromising customer trust.
13. Chaos Engineering for Security Resilience
Traditional security testing relies on controlled environments, which rarely mirror real-world attack conditions. Organizations often discover their incident response capabilities are inadequate only during actual security breaches! This reactive approach leaves businesses vulnerable to cascading failures.
Here, chaos engineering for security deliberately introduces controlled security failures into production-like environments. It also includes features such as:
- Simulated breach scenarios that test incident response procedures
- Automated pen-testing bots, “purple teaming as code,” and integrates with SIEM/SOAR platforms for instant incident validation
- Controlled system failures to validate security monitoring effectiveness
- Cross-team communication testing during security incidents
- Recovery time validation for critical security systems
These simulations include network breaches, data exfiltration attempts, and system compromises that mirror actual attack patterns. You can intentionally trigger security incidents to check the recovery mechanisms before facing real threats.
14. Edge and IoT Security Integration
The rise of edge computing and IoT devices creates distributed attack surfaces that traditional centralized security models cannot ‘adequately’ protect. These devices often lack security controls to make them attractive targets for attackers. Usually, traditional DevSecOps practices, designed for centralized cloud environments, fail to address the unique constraints of edge computing architectures.
Edge and IoT security integration extends DevSecOps principles directly into edge devices and IoT networks. It includes automated security policy enforcement, continuous monitoring of device behavior, and secure over-the-air update mechanisms that maintain security posture across geographically distributed infrastructure.
15. Secure Developer Experience & DevEx
Traditional security tools often create friction that slows development velocity. Complex security workflows, lengthy vulnerability reports, and manual compliance checks interrupt creative flow. This friction leads to security being viewed as a roadblock rather than an enabler. It results in developers postponing security considerations until later stages when remediation becomes exponentially more expensive.
Secure Developer Experience prioritizes seamless security integration within existing development workflows. It provides contextual security guidance directly within IDEs. These tools eliminate context-switching by embedding security capabilities into familiar development environments. The result is enhanced security posture achieved through developer-friendly tooling.
Conclusion
From AI-driven automation and autonomous remediation to cloud-native security, the future of DevSecOps is to embed security seamlessly into every stage of software development. With the latest trends, you can break down silos, automate threat detection, reduce business risks especially in a multi-cloud world.
At TechAhead, we understand that adopting these advanced DevSecOps practices can be challenging without the right expertise and support. As a DevSecOps consulting company, we follow the latest security protocols and compliance guidelines to ensure the best solution for your business. Our team of experienced software development and security professionals partner with you to design, implement, and optimize secure software delivery pipelines tailored to your unique business needs. Contact TechAhead today and let us help you leverage cutting-edge DevSecOps trends to drive innovation confidently.

Track mean time to remediation, vulnerabilities detected pre-production, deployment frequency, compliance scores, security incidents, and reduction in downtime to measure DevSecOps success and see improved ROI.
Yes, by using containerization, integrating security tools into existing toolchains, automating testing, continuous monitoring, and adopting a phased modernization approach, organizations can bring DevSecOps to legacy systems.
DevSecOps automates security, accelerates deployment cycles, reduces risks, and enables continuous delivery. It helps businesses quickly adapt to market demands and innovate while maintaining robust security throughout digital transformation.
Automate security checks in CI/CD, prioritize high-risk areas, embed security early (“shift left”), use integrated tools, and maintain cross-functional collaboration to maintain both rapid delivery and strong security.
Cross-training is essential as it bridges gaps between development, operations, and security. Cross training also boosts collaboration and encourages shared responsibility for security. It helps teams effectively manage evolving threats.




